VMware Cloud on AWS: Now What?

So you have VMware Cloud on AWS. What now?
You’ve sat patiently, watching the deployment countdown of your SDDC for the past few hours and it’s completed. Now what? Don’t worry. These things are always daunting when you’re new to them. In this post I will cover some of the most basic things you need to know to get logged in.
When you deploy an SDDC using VMware Cloud on AWS, it is configured with two networks: a management network and a compute network. The management network handles network traffic for the SDDC hosts, vCenter Server, NSX Manager, and other management functions. The compute network handles network traffic for your workload VMs. Two VMware NSX edge devices serve as gateways for the VMware virtualized networking environment. The management gateway (MGW) connects the SDDC management infrastructure to your on-premises environment. The compute gateway (CGW) provides connectivity for all workload virtual machines.
The VMC on AWS Management Network:
The management network you provided (or didn’t provide) during setup is utilized exclusively for VMware on AWS infrastructure. You cannot use this range for anything else, as it is consumed by VMware for your vSphere and appliance deployments. If you did not specify a network during deployment, you have been provided 10.2.0.0/16. The subnets 10.0.0.0/15 and 172.31.0.0/16 are considered “out of bounds” for VMC Management networks. You must select a /23, /20 or /16 CIDR for the management network. In short, expect to lose direct control of the addresses you provide for your VMC management network addresses as they are consumed by your cloud formations template.
VMC on AWS Networking Notes:
By default VMC will have created a network segment of 192.168.1.0/24 for you to utilize on your workloads. Network Segments can be managed from the “Segments” option under the “Network” heading. There are three types of networks.
- Routed, where the gateway is in the SDDC and can become accessible both publicly and to other routed segments within VMC.
- Extended, where the gateway is in another location. There are additional requirements and set up to extend Layer 2.
- Disconnected, which is an isolated or bubble network. This network will not have access to the internet or other machines outside of this particular network segment.
Configuring the Management Gateway Firewall:
First things first, we need access! After deployment is complete you can log into vmc.vmware.com and navigate to your SDDC. You’ll want to select “Networking & Security”, head to “Groups” under the “Inventory” header and then “Management Groups.” This is where you will create groupings of IP addresses that require access to your Management network. “Compute” would refer to where your VMs or workloads exist.


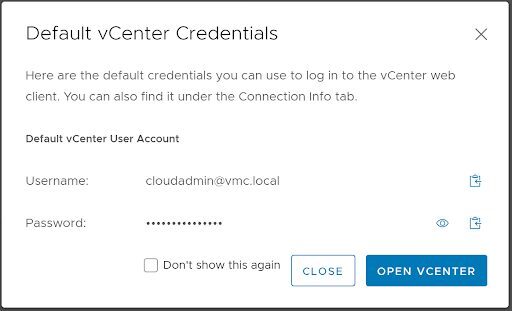
Now, head back to “Gateway Firewall” under the “Security” heading and select “Management Gateway”. Select “Add New Rule”. Create a name. “Set Source” as the group we just created that contains your Public IP address. “Set Destination” and select “System Defined Groups”. We will then want to select vCenter and hit “Save”. Under the “Services” field we will want to select at least “HTTPS (TCP 443)”. Publish your changes, click “Open vCenter”, “Show Credentials”, copy and/or view your login credentials and then select “Open vCenter”. Supply the username and password you procured in the last step and log in!


Deploying your first VM:
Now may be a good time to review the Storage Capacity and Data Redundancy doc from VMC. This will assist you in determining if there is a better storage policy for your VMC environment. Also note that it is best practice to use a storage policy of your own creation, rather than the default.
You can upload OVAs, OVFs and ISOs to your WorkloadDatastore just as you’re used to with a few caveats.
- You cannot deploy VMs to the Mgmt-ResourcePool
- You cannot deploy VMs to the Management VMs folder.
- You cannot deploy VMs to the vsanDatastore
- Network Segments must be managed from the SDDC Portal Manager rather than through vCenter
Once your VM is deployed, don’t forget to create firewall rules on your Compute Gateway, following similar steps to the ones listed in our section labeled “Configuring the Management Gateway”. The appropriate rules on your gateways will allow your VM to access the internet, other workloads, or even machines within your management network.

